After showing you the devastating attacks happening right here in Pennsylvania and the $10.5 trillion cybercrime industry targeting small businesses, you might be wondering if there’s any hope. Here’s the good news, there absolutely is. The businesses getting attacked aren’t necessarily unlucky, they’re unprepared. Protecting against AI cyber threats is a matter of preparation. And preparation doesn’t have to cost you a fortune or require an IT degree.
Let me share 10 proven strategies that will significantly reduce your risk of becoming the next victim, based on what actually works in the real world, not theoretical security textbooks.
The Reality Check. Small Business Cybersecurity in 2025
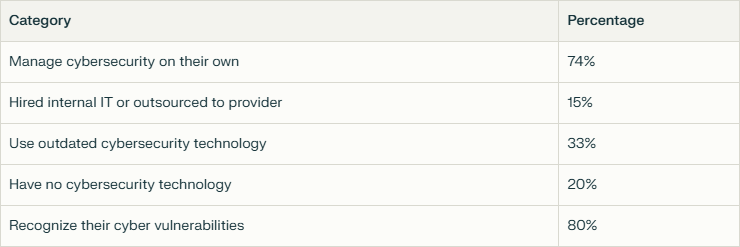
Before we dive into solutions, let’s acknowledge where most small businesses stand today. 74% of SMBs manage cybersecurity on their own, often without sufficient training, and only 15% have hired an internal IT professional or outsourced to a managed provider. 33% of SMBs are working with outdated cybersecurity technology, and 20% report having no cybersecurity technology at all.
But here’s what gives me hope: 80% of SMBs recognize their cyber vulnerabilities. Recognition is the first step toward protection.
10 Proven Protection Strategies That Actually Work against Cyber Threats
1. Implement Multi Factor Authentication Everywhere
This is your first line of defense against AI powered credential theft. Even if criminals compromise your passwords through sophisticated phishing, MFA can prevent unauthorized access by requiring a second verification method. This simple measure significantly reduces the risk of account takeovers from stolen credentials.
Action Step: Enable MFA on all business systems, email accounts, banking, and cloud services today. Use authenticator apps rather than SMS when possible.
2. Establish Verification Protocols for Financial Transactions
Create strict verification procedures for financial transactions, especially those requested through digital communications. Implement a multi person approval process for transfers above certain thresholds and require out of band verification like an in person conversation or call to a known number for unusual requests.
Action Step: Set up verification protocols and policies that require verbal confirmation for any financial request over $1,000, regardless of who appears to be making the request.
3. Fight AI with AI. Invest in AI Powered Security Tools
Small businesses should have an IT provider with AI powered security solutions that provide continuous monitoring and threat detection. These tools can help identify anomalous behaviors and respond to cyber threats in real time.
Action Step: Confirm your IT provider is using AI powered security solutions.
4. Conduct Regular Security Awareness Training
Receive ongoing training for you and your employees about AI specific cyber threats, particularly how to recognize deepfakes, voice cloning, and sophisticated phishing attempts. Make sure the training includes examples of AI generated content and establish clear procedures for verifying suspicious communications.
Action Step: Confirm your IT provider is providing security awareness training that includes AI and Phishing.
5. Keep Systems Updated and Patched Religiously
Make sure your IT provider maintains a rigorous schedule for updating and patching all software, applications, and operating systems to address known vulnerabilities that AI powered scanning tools might exploit. This fundamental practice remains one of the most effective defenses against automated attacks.
Action Step: Make sure automatic updates are enabled where possible and your IT provider is updating critical systems that can’t be automated.
6. Implement Network Segmentation
Your IT provider should be dividing your network into separate segments with different access controls to limit potential damage from a breach. By isolating critical systems and data, you can prevent lateral movement if an AI powered attack compromises one part of your network.
Action Step: Make sure you have separate networks for guest WiFi, employee devices, and critical business systems. Even basic network separation can significantly limit attack spread. A lot of of cyber threats are due to outdated software.
7. Deploy Password Managers Organization Wide
Use password managers to generate and store complex, unique passwords for all accounts. This prevents credential reuse that could allow attackers to access multiple systems if one set of credentials is compromised.
Action Step: Have an enterprise password manager and require all employees to use it.
8. Establish Comprehensive Backup and Recovery Procedures
Your IT provider should have a comprehensive backup strategy that includes regular, encrypted backups stored offline or in segregated cloud environments. In the event of a ransomware attack, having clean, accessible backups can prevent the need to pay ransom and allow for faster recovery.
Action Step: Make sure you IT provider has immutable backups. Test restoration procedures monthly.
9. Deploy Advanced Email Security Solutions
You should have email security tools that use AI to detect and block sophisticated phishing attempts before they reach employees. Solutions that analyze communication patterns, check for email spoofing, and scan attachments for malicious content, are something your IT provider should have.
Action Step: Make sure you have advanced threat protection that specifically addresses AI generated phishing attempts.
10. Partner with Cybersecurity Professionals
Consider working with cybersecurity experts who can provide guidance tailored to your specific needs. A good managed service provider offers security packages specifically designed for small businesses facing AI powered cyber threats.
Action Step: Talk to a cybersecurity first managed service provider in your area. Look for those offering comprehensive packages rather than single point solutions.
The RDCS Comprehensive Approach
Based on our service offerings, here’s how we implement these strategies for our clients.
24/7 Advanced Cyber Protection: Our US based Security Operations Center provides continuous monitoring with real time threat detection and response, including AI enabled endpoint protection that uses machine learning algorithms to examine end user behavior.
End User Security Management: We implement role based access policies, enterprise grade email security with filtering and encryption, and end to end device encryption.
Network Security and Administration: Advanced firewall management with custom security rules, 24/7 network monitoring, and comprehensive patch management to close vulnerabilities before exploitation.
Data Protection and Business Continuity: Automated backup systems with nightly offsite transfers, verified recovery processes, and complete disaster recovery planning with defined Recovery Time and Recovery Point Objectives. All our backups are immutable.
Measuring Your Security ROI
According to Kaspersky’s research, a business with 100 endpoints investing approximately $33,500 annually in cybersecurity can achieve an ROI of $71,830 if they prevent just one breach per year. When you consider that the average small business loses $25,000 from cyberattacks, and 60% close within six months of a successful attack, the ROI of cybersecurity becomes crystal clear.
Your Competitive Advantage
Here’s something most business owners don’t realize. Strong cybersecurity is becoming a competitive differentiator. Customers are increasingly choosing vendors based on their security posture. 47% of companies with less than $10M in annual revenue were attacked in 2024, but only 17% of SMBs have cyber insurance.
By implementing these 10 strategies, you’re not just protecting your business, you’re positioning yourself ahead of competitors who are still vulnerable.
Take Action Today
The cybercriminals aren’t waiting, and neither should you. Pick three strategies from this list and make sure they are in place this week. Then pick one more each month until you can verify you have a comprehensive defense.
Remember, perfect security doesn’t exist, but prepared businesses survive while unprepared ones become cautionary tales.
Book a 15-minute AI & Cyber Strategy Call to discuss which of these strategies would have the biggest impact on your specific business and how to implement them effectively.
FAQ
Q: Which of these 10 strategies should I implement first?
Start with multi factor authentication and financial verification protocols. These provide immediate protection against the most common attack vectors and cost virtually nothing to implement.
Q: How much should a small business budget for cybersecurity?
Industry experts recommend 3-5% of annual revenue for cybersecurity. For a $1 million revenue business, that’s $30,000-$50,000 annually, which can provide comprehensive protection.
Q: How do I know if my current security measures are adequate?
Reach out to us for a cybersecurity risk assessment to identify gaps. If you haven’t been professionally assessed in the last 12 months, your security posture is likely inadequate for today’s threat landscape.
Q: What’s the biggest mistake small businesses make with cybersecurity?
Treating cybersecurity as an IT problem rather than a business risk. Security needs to be integrated into every business process, not just managed by your IT person.