Cybersecurity Services to Protect you Business in Pennsylvania
Safeguard Your Business with Managed Cybersecurity Services. Stay Ahead of Hackers, Stay Secure.
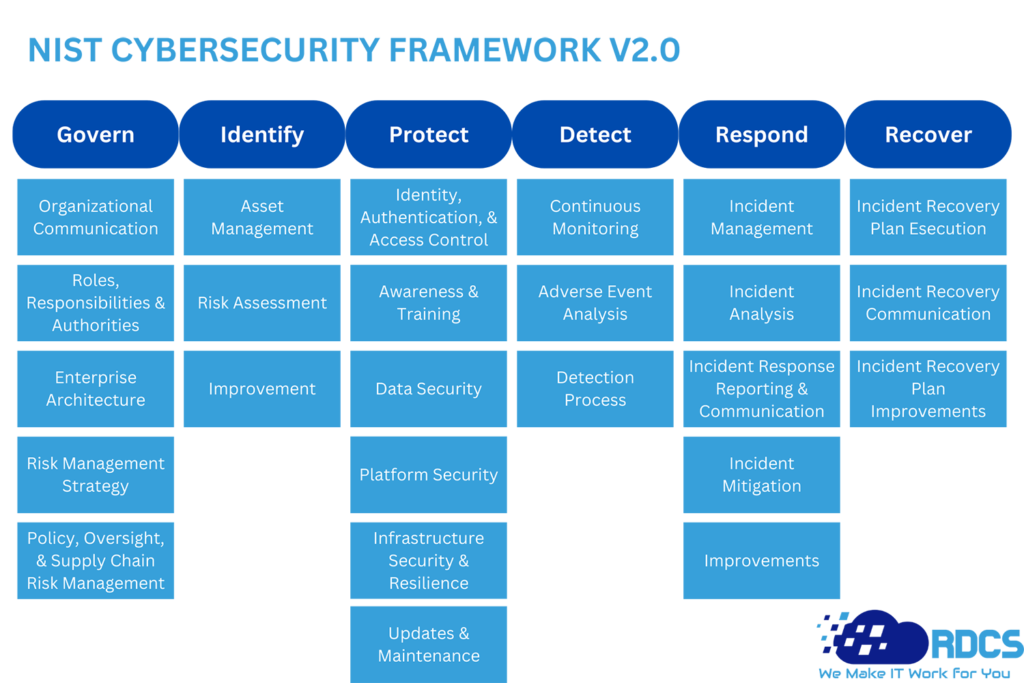
In an era where traditional cybersecurity measures no longer suffice, it’s crucial for businesses to adapt and evolve. Firewalls and anti-virus solutions, while essential, fail to fully combat the increasingly sophisticated cyber threats we face today. The rise of remote workforces, lucrative ransom payments, and advanced hacking strategies underscore the need for comprehensive cybersecurity services, particularly for small businesses.
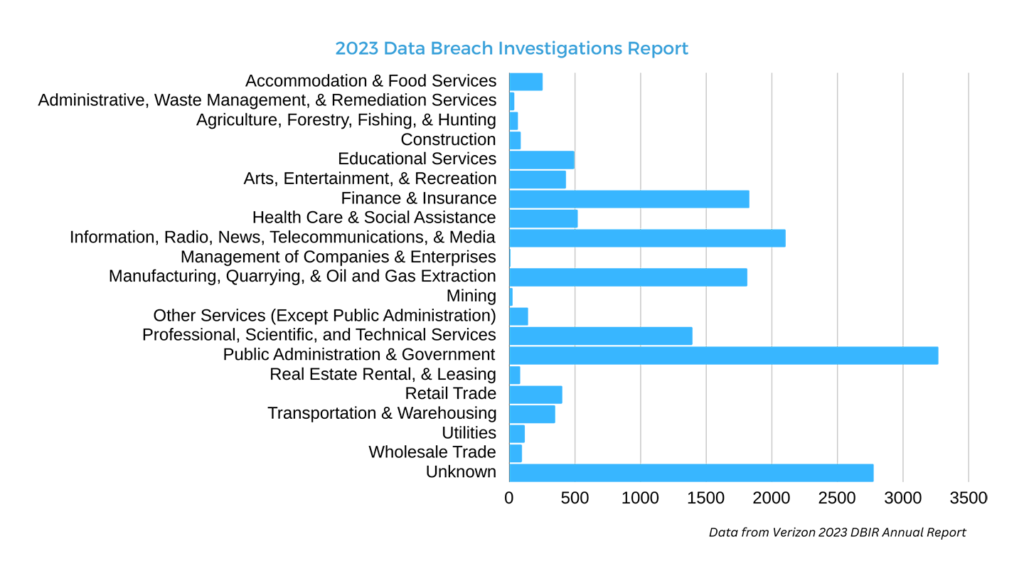
Cybercriminals are consistently on the prowl, ready to exploit vulnerabilities, steal sensitive data, or even lock you out of your own systems. These attacks can lead to substantial financial losses, with small businesses often being prime targets due to their lack of preparedness.
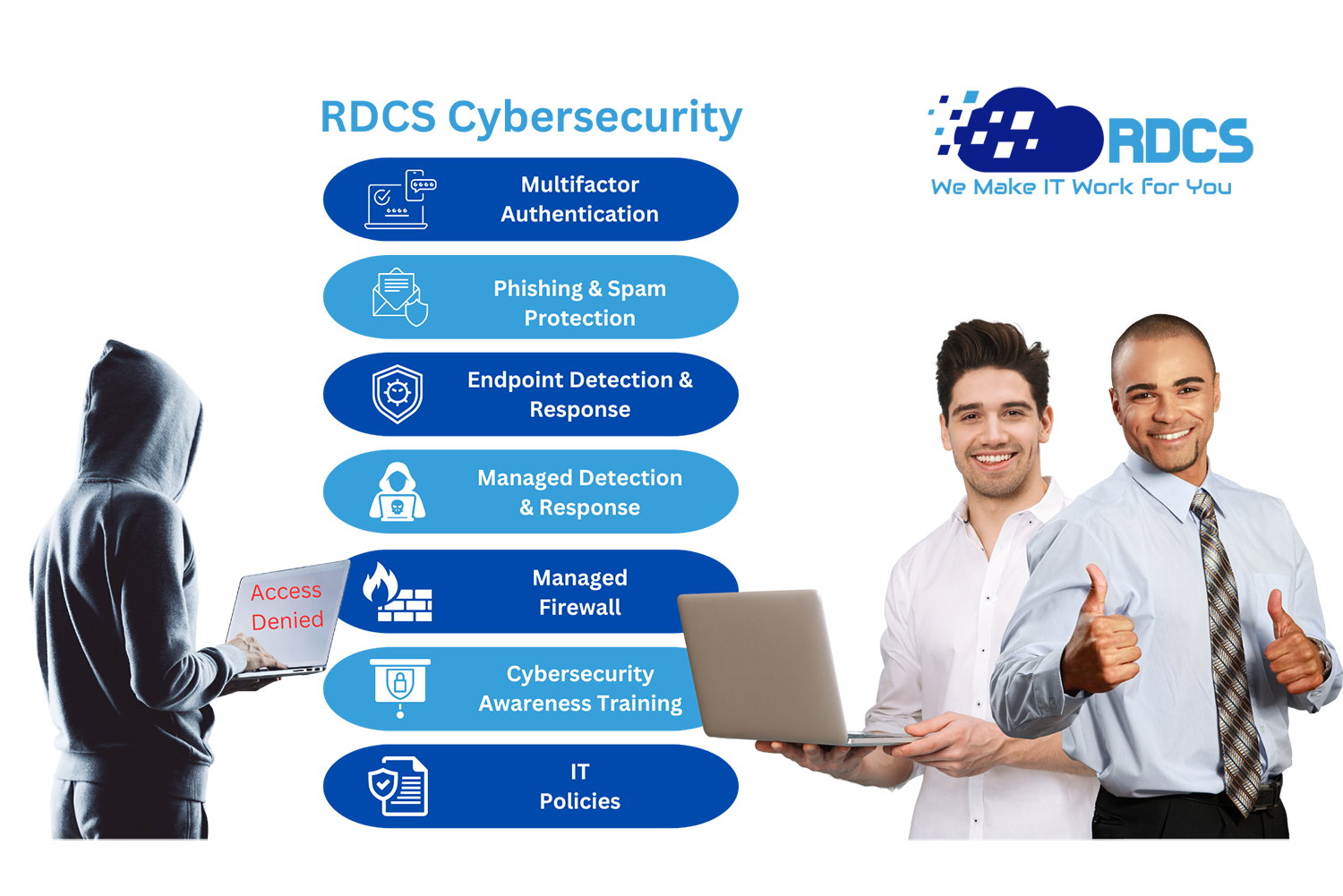
At RDCS, we aim to bolster your defenses by offering a variety of robust cybersecurity packages designed to keep you one step ahead of potential threats. As a customer-centric, professional, and reliable local cybersecurity company, we’re dedicated to securing your network, managing cyber threats, and educating your team to ensure your business remains safe.